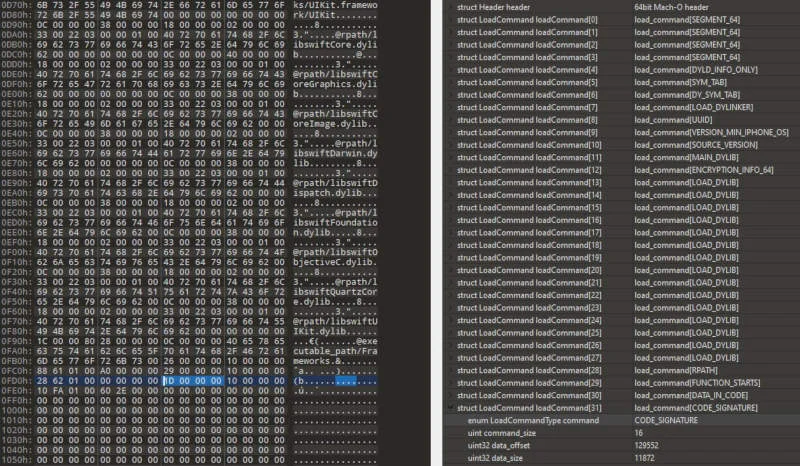
Abusing DLL Hijacking vulnerabilities in Windows Electron apps
9 minute read

Naz Markuta
18 October 2023
Email Security - Surveying big organisations' configuration
8 minute read

Scott Lester
21 November 2022
Vulnerability disclosure: how many top-million sites use security.txt?
11 minute read

Naz Markuta
26 October 2022
Analysing Mobile App Network Traffic with mitmproxy and StrongSwan
9 minute read

Naz Markuta
27 July 2022
It's tough getting going - technical decisions for start-ups
4 minute read

Rob Stemp
13 December 2021
Red Maple Technologies/IONOS Digital Transformation Case Study
1 minute read

Red Maple Technologies
9 December 2021
'Fun' with TLS - Automating the Testing of TLS connections
6 minute read

Lauren Palmer
17 September 2021
Video interview - Cyber security tips for small businesses
1 minute read

Red Maple Technologies
20 July 2021
Webinar - Digital Transformation and why you should consider Kubernetes
1 minute read

David Griffiths
3 June 2021
2020 Vision - A Look Back at a Year of Cyber Security
7 minute read

Red Maple Technologies
1 January 2021
Digital Transformation – it's not just the adoption of new technologies
7 minute read

Geoff Norton
18 November 2020