The first part of this blog introduced device management and some of the Intune basics. This follow-up covers all the initial setup required for getting Intune deployed.
Setup
Intune is all managed from the Endpoint Console, which as per usual, has a new UI coming out. There’s also device-related panels in the main admin page, the security pages, and AzureAD/Entra. The following sub-sections list most of the important parts of the various consoles.
Devices
The most commonly used page is probably the all devices panel:
Enrollment
After that, the enrollment panel is a shortcut to all the OS-specific enrollment options, of which there are many.
The typical enrolment options are probably going to be:
- Windows
Automatic Enrollment- with a couple of published DNS records, Windows devices can be enrolled by signing in with a valid email address or via Company Portal. For more information see here. - MacOS
Enrollment Program Tokens- is the Apple Business Manager mechanism for enrollment (see here). The other option is to use the Apple Configurator iOS App or Company Portal to manually add a device. - Android enrollment needs configuration of a profile or one of or both
Personally-owned devices with work profile(aka BYOD) orCorporate-owned, fully managed user devicesfor work-only devices.
Compliance and Configuration
There are compliance and configuration profiles for all platforms, which can be found centrally:
In this context, configuration is specifying settings, compliance is verifying the current settings against a standard.
It’s often easier to first go to the relevant device category and view the configuration there, as then it will only show you the relevant policies for that category. For example, under Devices > Windows:
Compliance profiles are applied as well as configuration profiles. They specify what’s expected of devices; non-compliant devices can be blocked from accessing company data.
When creating new configuration profiles for a platform you typically have two choices. Settings catalog allows you to select from the whole range of possible configuration options, whereas Templates has a range of pre-selected lists of settings from the catalog. The Settings catalog does have a search feature, but still presents dauntingly long lists of settings to enable and configure:
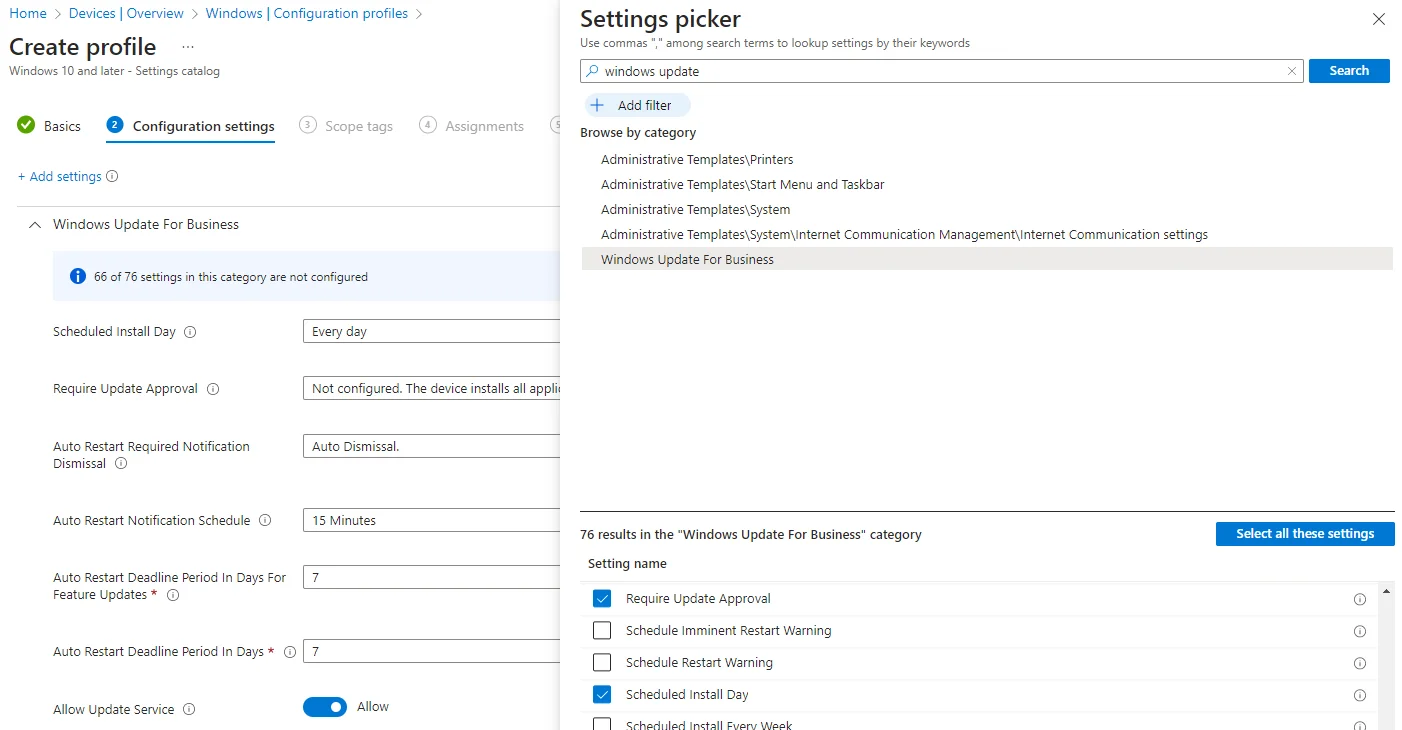
You’ll likely need a whole bunch of individual configuration profiles, and it’s easier to manage them if you keep them as separate and focussed as possible. For example, at Red Maple we currently have the following key profiles set for Windows (and others being tested):
| Name | Type | Purpose |
|---|---|---|
| Windows Application Guard | Endpoint protection template | Application Guard settings |
| Windows Chrome Settings | Settings catalog | Basic configuration for Chrome browser |
| Windows Device Restrictions | Device restrictions template | Lots of device configuration and lockdown settings, including the device password, DMA, and the lock screen |
| Windows Edge Minimum Settings | Settings catalog | Basic configuration for Edge browser |
| Windows Hello for Business | Identity protection template | Enabling Hello For Business |
| Windows Office (inc. macros) | Settings catalog | Disable macros, configure Office suite |
| Windows Office Auto-update | Administrative templates | Enable auto-update of Office |
| Windows office Wi-Fi | Wi-Fi template | The Wi-Fi details for our office |
| Windows Sharepoint Consultancy Sync | Settings catalog | Sync a SharePoint site for the consultancy team |
| Windows Update | Settings catalog | Windows update configuration |
For macOS, the Custom option under Templates lets you use a mobileconfig (XML) policy, such as the examples in the Intune samples GitHub repo. We have the following key macOS configuration policies set:
| Profile name | Profile type | Purpose |
|---|---|---|
| macOS 1Password | Custom | Configuration for 1Password |
| macOS Allow Screen Share | Custom | Allow screen sharing for Teams etc |
| macOS App Store | Settings catalog | Block the app store |
| macOS Block External Sharing | Custom | Block external sharing |
| macOS Chrome | Custom | Chrome Browser configuration |
| macOS Chrome Update | Custom | Chrome Browser updates |
| macOS Defender Anti-Tamper | Custom | Prevent Defender uninstall |
| macos Defender for Endpoint Full Disk Access | Custom | Defender config |
| macos Defender for Endpoint Network Filter | Custom | Defender config |
| macOS Defender Kernel Extensions | Extensions | Defender config |
| macos Defender MAU | Custom | Defender auto-update |
| macos Defender onboarding | Custom | Defender config |
| macOS Defender Settings | Settings catalog | Defender config |
| macOS Device Restrictions | Device restrictions | Device security restrictions, such as iCloud, password and other settings |
| macOS Disable Guest | Settings catalog | Disable the guest user account |
| macOS Edge Settings | Settings catalog | Edge Browser configuration |
| macOS Fingerprint | Settings catalog | Allow TouchID, with a timeout |
| macOS Login Window | Device features | Configure the login window |
| macOS Microsoft AutoUpdate | Settings catalog | Office auto-updates |
| macOS Office Notifications | Custom | Allow Office notification |
| macOS Office Settings | Settings catalog | Other Office settings |
| macOS Office Wi-Fi | Wi-Fi | The Wi-Fi for our office |
| macOS OneDrive | Custom | OneDrive configuration |
| macOS Profile password | Settings catalog | Prevent the management profile being removed |
| macOS screensaver lock | Settings catalog | Enable screen timeout |
| Microsoft Enterprise SSO | Device features | Enable m365 SSO |
It’s a long list, partly thanks to Defender needing different bits of config.
The last one is particularly welcome by users - it allows users to sign in once to all Microsoft apps (see here for more).
Many of the device configuration settings are also available in dedicated sections under endpoint security:
More on that in the next section.
Finally, there’s app protection policies. These are technically configuration policies, but can be set from the Apps menu. They are used to setup work containers on BYOD devices, and what’s allowed between work and non-work apps. A prime example here is allowing the Outlook in the work container sync local contacts and calendars.
Security Configuration
There’s a whole section in the Intune console devoted to Endpoint security:
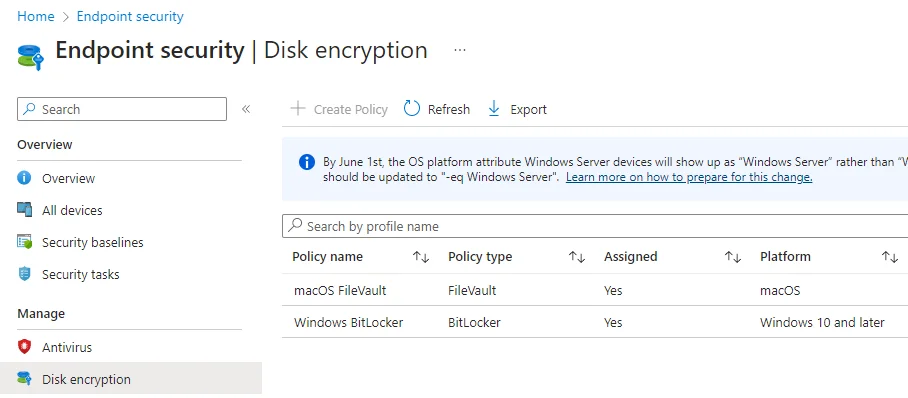
This includes, for example, settings for disk encryption and anti-virus:
Alternatively, it can all be set in the Defender portal. Configuring it in Intune means it won’t be available in the Defender portal, although they do offer a handy button to move across:
There is also an overlap with what you can set via device configuration policies and here in the Endpoint Security section.
Apps
The Apps panel is where you can specify which applications are available per platform. They can be assigned to devices and groups as either required (will be installed automatically) or optional (will be available to manually install via Company Portal).
In general and regardless of the platform, apps can be added either by selecting them in the respective app store, or via an installation file. The latter method is, unsurprisingly, the more complicated approach.
All licensed Apple apps have to be bought or added in Apple Business Manager for the tenant, and connected via the Apple VPP connector in Intune. If available via DMG or PKG they can be added in Intune as a macOS line-of-business app.
That’s all we’ll cover here. There are lots of intricacies to adding apps in Intune, but also lots of documentation.
Device Administrators
The setting for which domain accounts can authorise administrator actions on a managed device is, for some reasone, in AzureAD, specifically Devices > Device Settings, under Manage Additional local administrators on all Azure AD joined devices.
Advanced Stuff
Importing and Exporting Policies
Intune policies can be defined as ADMX files and imported and exported using PowerShell, or using tools such as IntuneManagement, which wrap PowerShell.
Scripts
The Intune console includes a place for scripts. We’ve found these most useful for Macs, where the Microsoft Intune samples on GitHub has some good examples, including one for tidying the Dock and one for installing Zoom.
Zero Touch Enrollment
With zero-touch enrollment (their jargon, not mine), devices purchased through Apple Business Manager or an Autopilot OEM programme (such as those from Lenovo, Dell and HP) are automatically added to Intune, from where they can be assigned to a user without administrators having to first touch the device. This means devices can be purchased and sent directly to users, and will be managed from first boot.
Shared Devices
In contrast to the user affinity model, you can also create shared devices. For example, at Red Maple we use this for a cheap laptop that’s only used at conferences and events.
On Windows, for example, it means that the guest user is enabled but is wiped on logout. Microsoft 365 users can sign in using their company email address and access company resources, but the profile is also wiped on logout. You can optionally restrict access to the hard drive - it’s all set up using device configuration profiles, for example:
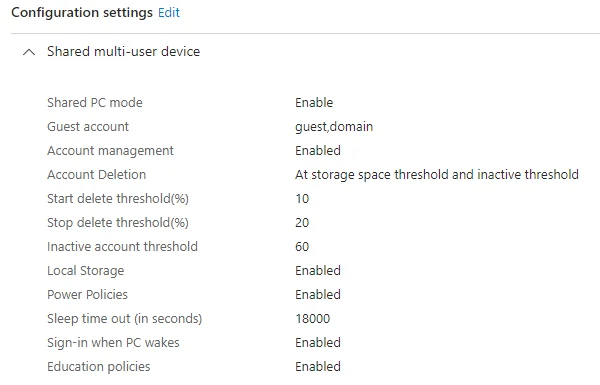
One requirement to get this working is setting up device categories, as described above, which allows users to select shared device on initial setup. This can probably also be achieved using device groups.
For more on shared devices, see this great blog.
Customising Company Portal
You can do lots to make it look like a branded application, all from this console in Intune






