The UK National Cyber Security Centre recently published a comprehensive guide on tips to protect government domains that don’t send emails from being used to conduct spoofing or phishing attacks. However, as good as the information is, there is always room for improvement…
Protecting Subdomains
The advice does provide a great summary of how to address a spoofing issue that many IT security staff may not have previously thought about. However, in the latter section, it says:
if you want to protect subdomains that send email, you must:
- use
sp=noneinstead ofsp=reject.
We think this bit of advice can be improved upon. The problem is that having sp=none set on your root domain re-enables email spoofing on vulnerable subdomains that do not have a DMARC policy. All the attacker needs to do is setup their own mail server and domain name, find a vulnerable subdomain, and then send a spoofed email by changing the return-path header to that of the vulnerable subdomain.
Example Records
Take the gov.uk domain for example. It contains the following DMARC and SPF DNS records:
~ dig +short txt _dmarc.gov.uk
"v=DMARC1;p=reject;sp=none;np=reject;adkim=s;aspf=s;fo=1;rua=mailto:dmarc-rua@dmarc.service.gov.uk"
~ dig +short txt gov.uk
"d1v9gv6rnax070.cloudfront.net"
"_globalsign-domain-verification=ODfp1IOZm7yaM-mgboc0-ixg1nqMxH8Kl3JAny9ip3"
"v=spf1 -all"
This domain does a really good job at preventing spoofed emails using non-existent subdomains, using the np=reject record. For example, doesnotexist.gov.uk contains a DNS record:
~ dig +short txt _dmarc.doesnotexist.gov.uk
"v=DMARC1;p=reject;rua=mailto:govuk-rua@dmarc.service.gov.uk"
However, a genuine subdomain in use, like data.gov.uk does not have a DMARC DNS record, which means it is vulnerable to email spoofing, because the gov.uk domain contains a sp=none policy and this subdomain doesn’t have its own record, as shown by a quick DNS lookup:
~ dig +short txt _dmarc.data.gov.uk
[EMPTY RECORD - DOESN’T EXIST]
Abusing Subdomains
The example below shows a spoofed message from noreply@data.gov.uk, sent to a Google Mail account. Google displays a via text next to the from address when the domain in the Return-Path address and From address do not match.
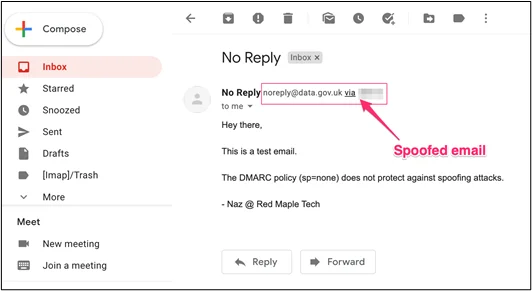
That’s a good thing to look out for in general, to help spot suspicious emails.
Taking a closer look at the email headers:
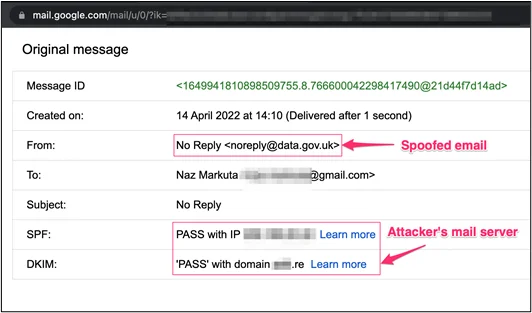
Google mail gives us a PASS for both SPF and DKIM check, since we’ve applied legitimate DNS records for our own domain. But notice that the From address is different to the DKIM (our domain custom ending with .re).
Conclusion
When using the sp=none policy on the root domain, it’s important that subdomains must also have their own DMARC record. Otherwise, it may be vulnerable to direct email spoofing attacks by abusing the return-path header.
Instead of sp=none, use sp=quarantine policy on the root domains to protect subdomains (that exist) that do not have a DMARC record. This way emails are automatically moved to the spam/junk folders when DKIM/SPF checks fail.






