If you have got yourself a nice new Pixel 6, and happen to be on PlusNet broadband, have you noticed that the update feature doesn’t work? That happened to me, and with a bit of technical investigation I figured out the problem: It’s PlusNet’s parental control filtering.
The Pixel Problem
After having my Pixel 6 device for a number of months, I was chatting with a colleague and we happened to get onto the exciting topic of Pixel 6 updates. I was surprised to discover that my device had not installed any updates since I purchased it a number months ago, despite updates being available and pushed out by Google. My phone knew that updates were available, but seemed unable to download the update package, as shown in the screen recording below.
The update process was stuck claiming ‘Download Paused’. Pressing the ‘Resume’ button seemed to cause it to attempt to download, but immediately return back to the ‘Download Paused’ state.
Tracking down the root cause
I’ve included both a long and short version… jump straight to the short version if you do not want to know all the gorey technical details.
The long version
So, what was going wrong? This was a tricky problem to track down, as there was zero debugging information available. After jumping through a number of hoops, I was able to get a Wireshark capture of network traffic from my phone which allowed me to inspect the raw packets. It became apparent that when attempting to download a firmware update, my phone would attempt to connect to the following server:
ota.googlezip.net
Applying filtering to my Wireshark capture allowed me to isolate the traffic between my phone and the update server and revealed the following:
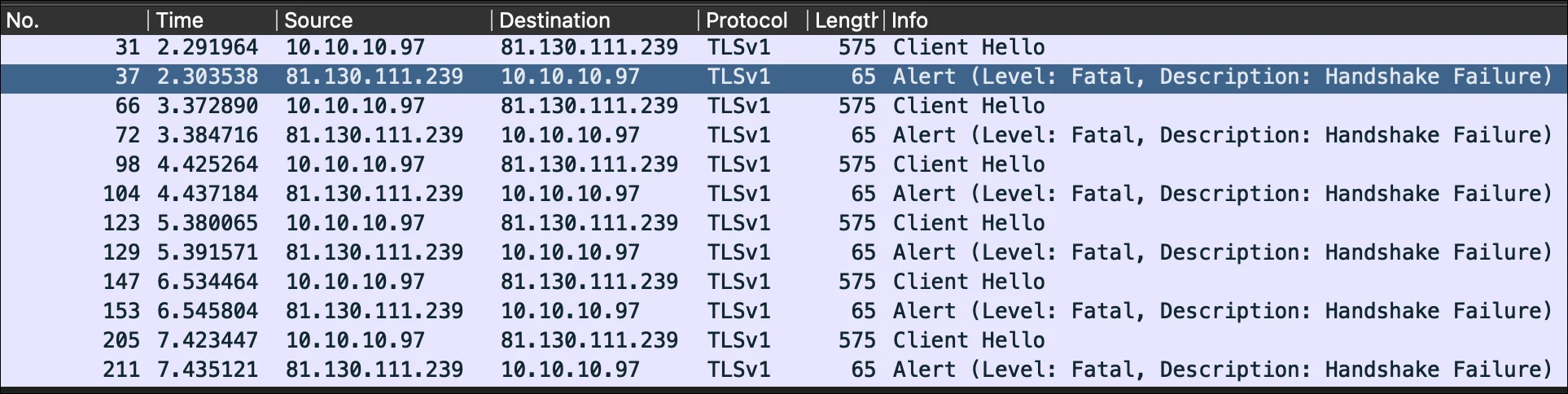 This shows that the secure handshake between the phone and the server was failing. Bizarre!
This shows that the secure handshake between the phone and the server was failing. Bizarre!
Digging deeper, and performing a WHOIS enquiry on the IP address of the update server, I discovered that it was part of a pool of IP addresses belonging to BT.
% Information related to '81.128.0.0/12AS2856'
route: 81.128.0.0/12
descr: BT Public Internet Service
origin: AS2856
mnt-by: BTNET-INFRA-MNT
created: 2005-06-16T14:11:53Z
last-modified: 2014-07-31T07:47:16Z
source: RIPE # Filtered
This seems strange for one of Google’s backend services?
It all became clear when I pointed a web-browser at http://ota.googlezip.net and followed the returned 302 redirect…
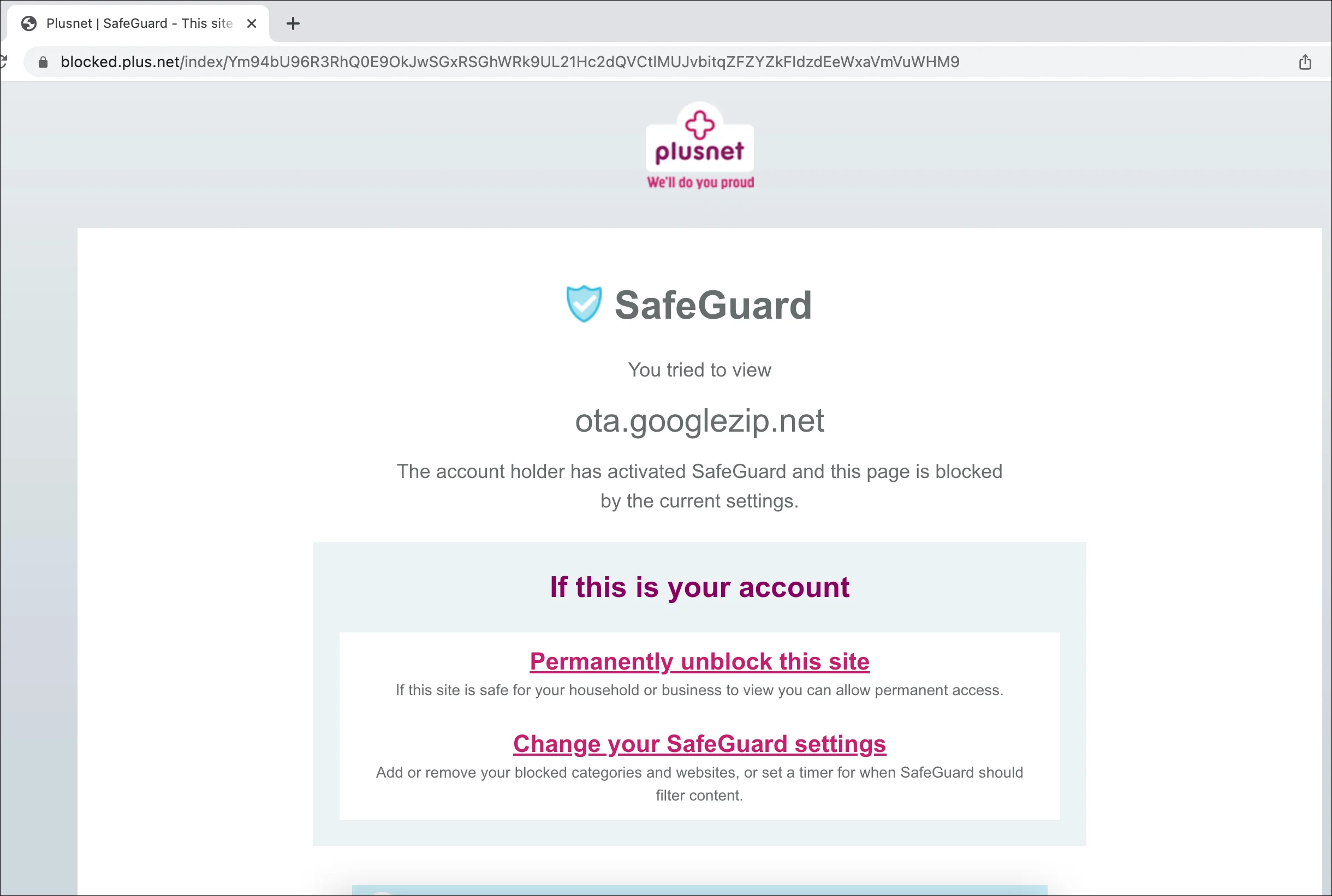
My home broadband is provided by PlusNet and their SafeGuard service (their content control functionality) seems to be blocking the update URL!
Another interesting discovery - when I pointed my browser at https://ota.googlezip.net (i.e. the https variant if the page) I received the following error:
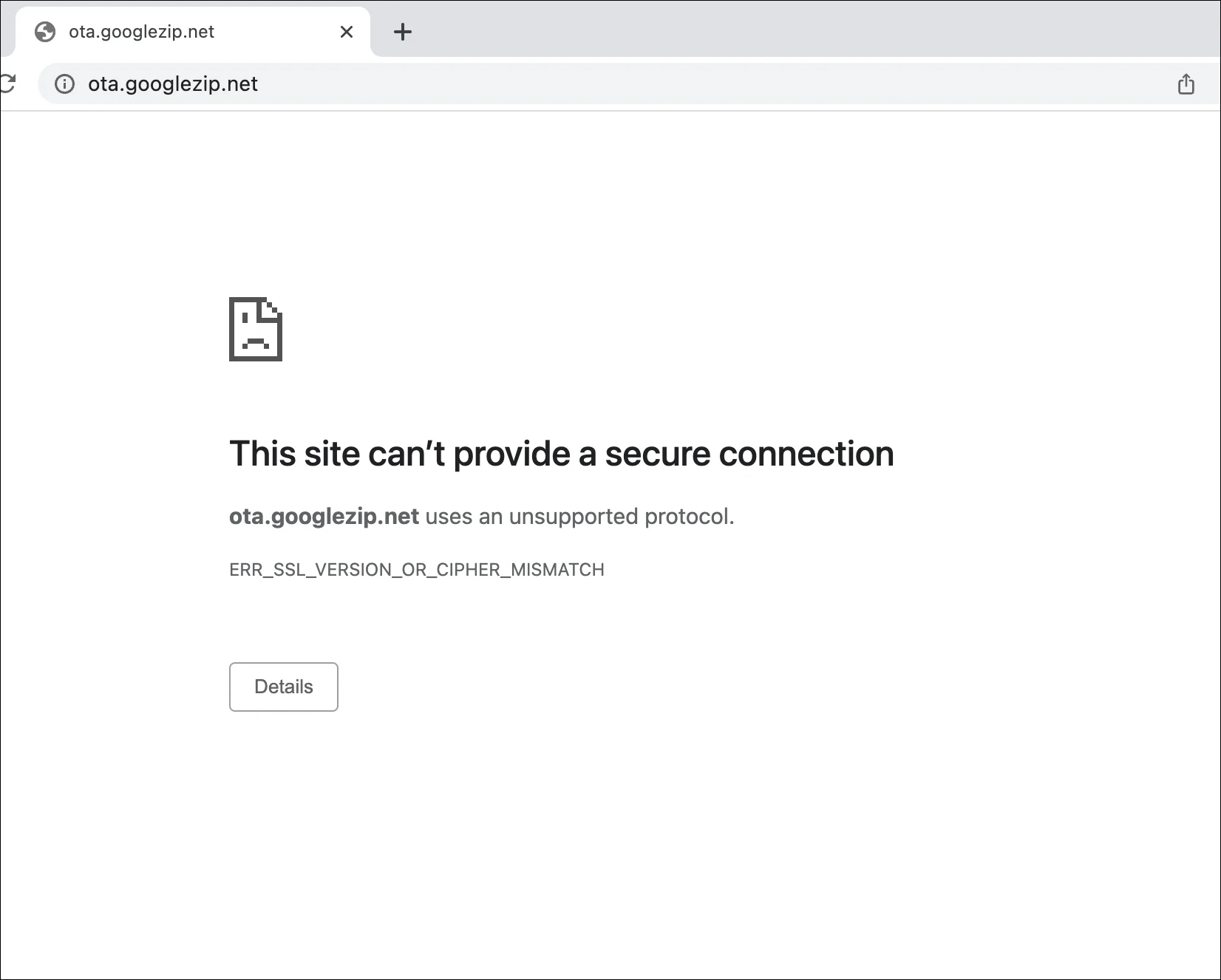
It seems that the server performing the redirect does not support any of the modern TLS cipher suites that browsers now mandate. If a customer were to request the https variant of a blocked site, they would receive this rather unhelpful messages, rather than the blocked page message.
The short version
Plusnet’s parental control filters were blocking access to the update server where Google serve the Pixel updates from.
Who’s at fault?
I feel that the lion’s share of responsibility needs to fall with PlusNet. Their parental control filtering is blocking a legitimate domain that is used to provide critical security updates to customers’ mobile devices. I am not the only person who has experienced this issue; it has been reported on their community forums and a forum administrator has responded, yet three months on, the issue still exists.
However, I also feel that Google could make the update process on the Pixel range of devices smarter. The device knows that there is an update available, but cannot download it - I feel it should do a better job of passing a sensible error message to the user rather than silently failing in the background.
How can I fix this
For those people with a new Pixel device, there are a few possible resolutions to this issue:
- Specifically allow
ota.googlezip.netin the SafeGuard configuration on your broadband connection. This can be done in the SafeGuard Control panel screens within your PlusNet account management pages.
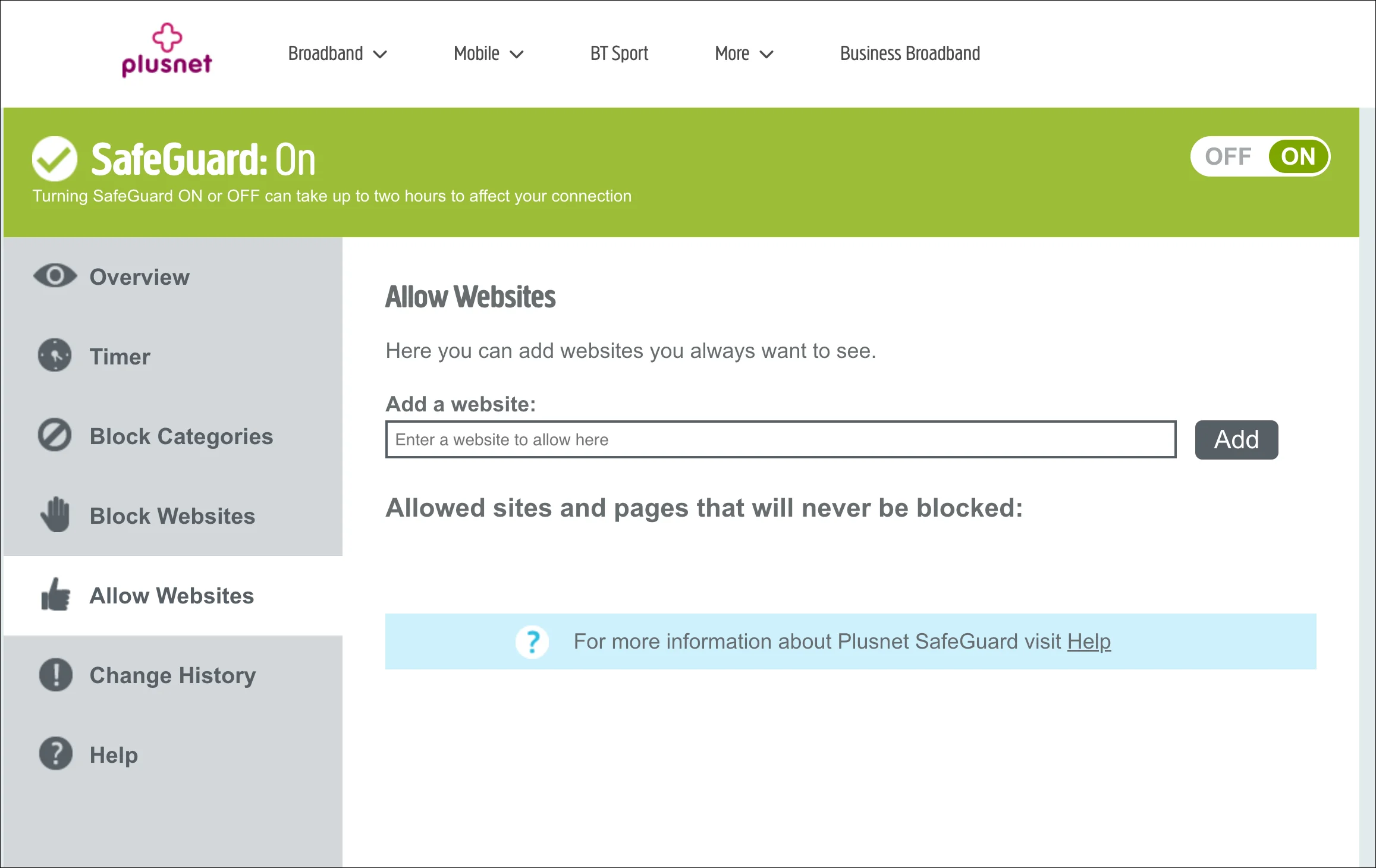
- Depending on your household, turning SafeGuard off completely could be an option?
- For those that have a mobile plan with a large data allowance, you could enable the option to download updates over your mobile data connection.
Conclusion
This article illustrates that the parental control mechanisms implemented by our ISPs can unexpectedly disrupt core functionality of modern devices. In this scenario the mechanisms established to try and protect consumers actually places them at increased risk, by stopping them receiving the latest vendor critical security updates.
We are hoping to raise this issue with PlusNet and Google in an attempt to get this resolved - we will update this post with details of any response that we receive.





