Affected products
The Iris mobile app from Crocus, version 1.3.7 and related backend API (iris-api.crocus.co.uk).
It’s available on the Apple App Store and the Google Play Store.
Note: all issues mentioned in this advisory have now been fixed.
Risk
Leakage of Personally Identifiable Information (PII), specifically email addresses and full names of all registered users. The only requirement is having a registered account, or more specifically, a valid authorization bearer token.
Summary
We found four issues found with the app and its backend API:
- Account email addresses are leaked on community posts and comments.
- Account authentication token remains valid for at least 30 days.
- Account registration accepts easily guessable passwords.
- No account rate limiting and detection of unusual requests.
PII Leakage
The mobile app communicates with an API server (iris-api.crocus.co.uk) for querying database records. This includes data held for a community feature where users are able to view and create posts. The menu is available from the “My Feeds” or “Explore” within the app.
The API server responds with JSON object, which contains two key fields called postCreatedBy and userDetails, both of which revealed the info of other registered users.
Below is a list of affected API endpoints, which leaked the poster info:
/api/v1/posts/browse/api/v1/guest/{userId}/profile/api/v1/guest/{userId}/posts/api/v1/me/feeds/api/v1/me/post/react/api/v1/post/{postId}/details
The first API endpoint above lets you browse all community posts. At the time of writing there were approximately 1638 posts. This was down to the parameter (?page=) which specifies the page number.
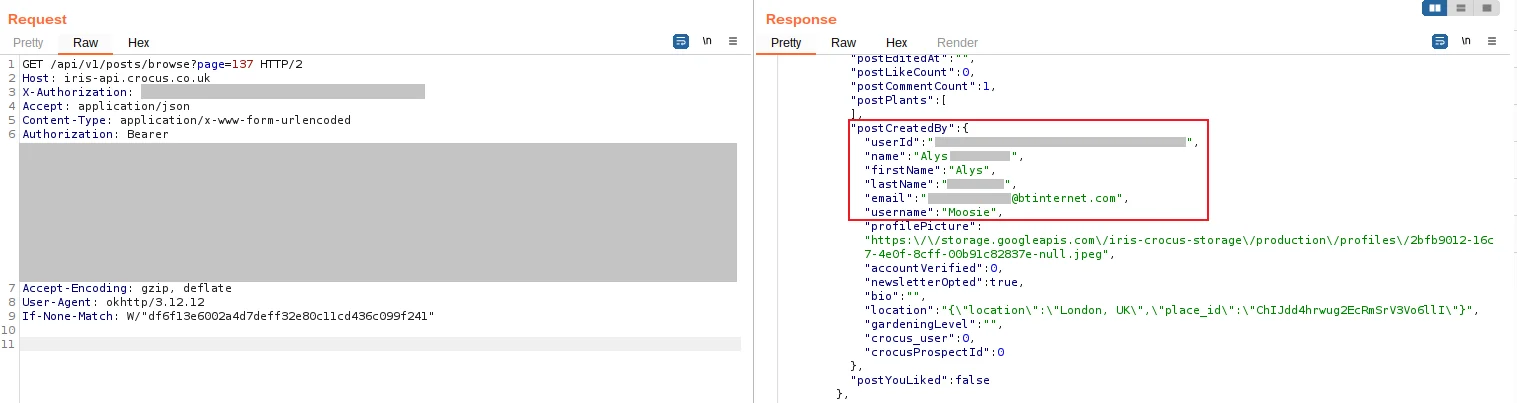
Below is a screenshot of an API request (/api/v1/posts/browse) showing user details:
Here is a screenshot of a different API request, which filters by a (userId):
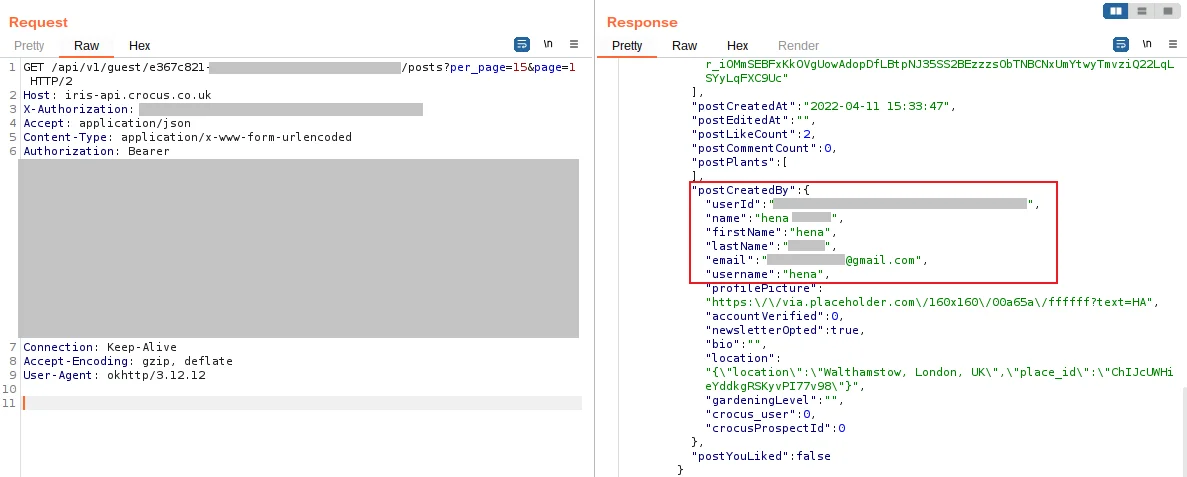
Attackers could go through each post or comment, and obtain a collection of email addresses, user IDs, and full names. This information could then be used to sell for email spamming or for phishing attacks.
In some cases users can also supply their location with a post.
Authorization Bearer Tokens
The app uses an HTTP header called Authorisation Bearer: xxxx, which contains a unique string appended to every request. These tokens are used to verify a user’s identity, which also serves the purpose of restricting access to certain types of information and content from the backend API server (iris-api.crocus.co.uk).
Our testing revealed that these authentication tokens remained valid for at least 30 days. A token from (11 Apr 2022 15:56:20 GMT) was retested at (18 May 2022 13:12:43 GMT) was found to be still valid. We recommended setting an expiry date for all user tokens. Or rotating authentication tokens when a user opens the mobile app.
Weak Password Requirements
The password requirement for the app is very weak, as there are no restrictions on what users can choose as their password. For example, users can register an account using password1 as their password. We recommend applying stricter password policies and forcing users to pick a strong password during account sign-up.
No Rate Limiting
Furthermore, in all the API requests there were no signs of rate limiting, or how many times a user can send a request before being blocked. This means a logged-in attacker can abuse the API like harvesting email addresses, without worrying about getting blocked or throttled.
Disclosure timeline
- 11 Apr 2022 - Initial issues discovered
- 19 May 2022 - Sent security disclosure report via Which?
- 17 Jun 2022 - Issues fixed (confirmed by re-running check)





